Friday, December 28, 2012
How to clean up the Add or Remove Programs tool utility in Control Panel
When uninstalling a program, you normally click on the Remove button on the Add or Remove Programs tool utility. It will ask you for confirmation to uninstall the program and once the program has been uninstalled, the program name entry will be removed from the list. However, when the Remove button does not work, and the program stays on the list (instead of asking for the confirmation), you can remove the entry from the list by deleting the registry entry on the Registry Editor. Extreme care should be taken when working on registry entries.
How to remove the program entry on the Add/Remove Programs tool:
1. Click Start -> Run.
2. Type regedit.
3. Click OK. The Registry Editor will open.
4. Go to: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall.
5. Find the key you want to delete (example: Mozilla Firefox 12 x86).
6. Save a backup of the registry key: On the Registry Menu, Export the registry key. Import this key later if necessary.
7. Delete the selected registry key and its values. WARNING!! Do not delete the entire Uninstall key.
8. Close the Registry Editor.
9. Check to make sure the program entry has been removed: Click Start.
10. Control Panel -> Add or Remove Programs.
Sunday, December 16, 2012
How to Secure your Computer Network
What is a computer network?
A network is a system of interconnected computers which can communicate, share resources and transfer data. The Internet is an example of a computer network.
We have seen and experienced the tremendous advantages and benefits of computer networks, but as the computer technology advanced so are the crimes in the computer industry. Identity theft, unauthorized access, illicit downloads, scams, computer viruses, spywares, adwares, malwares, trojans, worms, hijackers, trackwares, dataminers...the list goes on, these are just few of the bad things that we want to stay away from. There can be no such thing as completely secure network, but with useful knowledge and with the help of security tools, the risks and dangers can be minimized. Below is a list of practical and basic means of safeguarding your network as well as yourself.
Top 10 ways of securing your network:
PROTECT THOSE VULNERABLE WIRELESS NETWORKS
When you purchased those wireless routers, they are mostly designed so that it is easy to setup and install, but the problem is that security features are being compromised and disabled. To provide security to your wireless network, follow these steps:
- Change the default password of your wireless router
- Change the name (SSID) of your wireless router
- Disable SSID broadcast on your wireless router
- Enable WEP or WPA encryption on your wireless router and on your wireless network adapters
USE PASSWORDS THAT ARE HARD TO GUESS
Once your password is stolen or cracked, your personal information will be taken and your accounts will be in danger. To secure your passwords, follow these steps:
- Don't make obvious and easy to guess passwords, instead use a combination of characters, numbers, capital letters, and signs
- Choose a different password for each of your accounts
- Keep your passwords secret, and if you wrote it down, store it in a safe place
- Change your passwords on a regular basis
or when you feel it is being known by someone else
- Never use the "Remember password" option, your laptop computer may be stolen and your files can be easily accessed
USE ANTIVIRUS
A computer virus may corrupt valuable files or even delete files and directories, trigger a computer crash, or even shutdown an entire operating system, and other harmful and unpredictable damages. To protect your network:
- Make sure an effective antivirus is installed on every computer on the network
- Enable active, resident, or real-time protection
- Schedule regular automatic virus scans
- Configure the Antivirus program to automatically receive updates (virus signatures)
USE ANTISPYWARE, ADWARE BLOCKER, POPUP BLOCKER
Spywares are malicious programs intended to gather information (spy) from your computer. Adwares are annoying programs that popup advertisements (usually banner ads) to promote another site and thereby increase traffic. To get rid of all these kinds of troubles on your network,
- Install antispyware, anti-adware and popup blocker on every computer on the network
- Enable active, resident, or real-time protection
- Schedule regular automatic spyware and adware scans
- Setup the Antispyware, Adware blocker and Popup blocker programs to automatically receive updates
USE FIREWALLS
Broadband, high-speed connections which are always on are perfect targets for hackers, thieves, and frauds. Firewalls are used to prevent these cheaters from obtaining access to your network. To ensure protection, make sure to setup and install a firewall on each computer on the network, then, periodically check the firewall rules to give access only to the programs allowed and trusted by you.
INSTALL ENCRYPTION SOFTWARE
Even when your computer is lost or stolen, encryption software can provide a further protection of sensitive data and information. If the file is encrypted, it can not be readily read by thieves and attackers, thus delaying their dirty work and giving you extra time to do the necessary actions.
USE PARENTAL CONTROL PROGRAMS
Talk to your children about the dangers that the Internet poses. Warn them not to give out addresses, birthdays, names, and other private information. Review the website history to determine the places your kids went into. To minimize the online risks, allow your children to only use the computer when you or any responsible adult can monitor and watch them.
BEWARE OF PHISHING SCAMS
Phishing is a method of identity theft designed by scam artists that is implemented by sending emails to unsuspecting victims in order to trick them to provide their personal data such as passwords, credit card numbers, bank account numbers, and other personal and financial information. The usual tactic is to tell to the victim of the urgency that their account is about to expire or be soon suspended. A link is then provided for the victim to click which then leads to fake website (but authentic-looking) then the victim is lured to provide sensitive information. To avoid being a victim of phishing emails:
- Real banks and financial institutions don't request confidential financial information via email, don't ever open or read these emails
- Don't click on any links within the phishing email
- Never reply or send any emails asking you for private personal information on your account
AVOID PONZI, GET-RICH SCHEMES, FRAUD E-MAILS
Ponzi scheme (named after Charles Ponzi) is a deceptive investment strategy which promises quick and high returns in order to entice new investors. Payments to investors actually come from new investors' money and never from the fraudulent company.
Multilevel Pyramid scheme is a fraudulent business in which a prospective investor is ask to make one payment and then to recruit a new investor who would also make a payment. The first investor is offered a sum of money as a result of his recruit. The new recruit then recruits other people and the process of recruiting goes on and the more downlines, the more profits being promised.
CREATE BACKUPS
Backups are important data recovery and network security method. If a virus or other malicious software or program corrupted all the files on the network, you have something to go back to. The significance of backing up your files is also realized when problems arise such as accidental file or folder deletion, hard drive malfunction or failure resulting in data loss, stolen computers and drives, fires, floods, earthquakes and other damages.
How to add an exception to Windows Firewall
What is a Firewall?
A firewall is software or hardware that either allows or prevents information from the internet to go to your computer. A firewall is a safety feature to your computer so that you have protection against intruders or hackers trying to spread virus or simply stealing your personal information.
What is Windows Firewall?
Windows Firewall is a software program as part of Microsoft Windows whose purpose is to block incoming network connections from the internet so that they can not pass through or communicate with your computer. It will protect your computer from virus, spywares, worms, and other malicious programs by denying them to connect to your computer. According to your preference settings you can set the level of protection by adjusting from the menu. Windows Firewall is automatically installed if you install Windows. Windows Firewall is ON by default. It is recommended to Always let Windows Firewall ON for maximum protection. In Windows Firewall, you can either block or unblock programs. You can also block or unblock specific ports. However, if you want trusted programs or software to access your computer, you need to Allow them, so you need to Add an exception in Windows Firewall.
How to add an exception to Windows Firewall:
1. Click Start button.
2. Click Control Panel.
3. Double click Windows Firewall.
4. Click Exceptions. Note that the Programs and Services with a check mark means they are Allowed by Windows Firewall.
5. To add a program, click Add a Program, Browse or Select the program and click Ok. To add a port, click Add a Port, type the port Name, enter the Port Number, select TCP or UDP, and press OK. A program exception is more secure than a port exception.
6. To enable Windows Firewall to your Local Area Connection, Wireless Network Connection, or 1394 Connection, just click on Advanced and put a checkmark on these Network Connections.
How to add bullets in Notepad, Word, Powerpoint, Excel (keyboard shortcuts)
It depends on the user but some people prefer mouse clicks, touchpad clicks, and keyboard shortcuts. Sometimes you find it very convenient to know and use the keyboard shortcuts. It allows faster typing and even relaxes the fingers. I have gathered here the keyboard shortcut on How to add bullets in Notepad, and in commonly used Microsoft Office documents namely Word, Powerpoint, and Excel.
How to add a bullet in Notepad:
a.] Press the Numlock in your Numeric Keypad.
b.] Press and Hold the ALT button.
c.] While holding the ALT button, Press any of the following numbers on the Numeric Keypad.
4, 7, 8, 9, 10, 16, 175, 249, 250, 254, 0149 (bullet style differs depending on the number and font set)
d.] Release the ALT button.
How to add a bullet in Word:
Keyboard shortcut: CTRL + SHIFT + L ---> dark circle bullets
Menu: Click Format --> Bullets and Numbering
How to create bullets in Powerpoint:
Keyboard shortcut: ALT + O + B
Keyboard shortcut: Shift + F10 + B
Menu: Click Format --> Bullets and Numbering.
How to put bullets in Microsoft Excel 2010:
1. Put cursor into the cell.
2. Use the keyboard shortcut Alt + 7.
*. Also you can use the keyboard shortcut Alt + 9.
How to change lowercase to UPPERCASE letters in Word
Microsoft Word has powerful features that can change letters from Uppercase to Lowercase and vice versa. It can also change the case of a sentence (making the first letter of the sentence in capital). There is also an option to make a Title Case. This will make the beginning letter of the sentence in capital. Example, "how to change lowercase letters to uppercase in word". When you select the Title Case option, the result would be "How To Change Lowercase Letters To Uppercase In Word". Notice the capital letters at the beginning of each word. Microsoft Word is very flexible as you can convert from lowercase to uppercase by using two keys. The keyboard shortcut is by pressing Shift and F3 together. You can also convert each letter in a word or sentence from uppercase to lowercase and the opposite. Example, "MicroSoft Word" would then become "mICROsOFT wORD". This is the toggle case scenario which will change a letter from capital to lowercase and from lowercase to uppercase within the word or words within the sentence or paragraph or paragraphs. Below is the procedure for each scenario.
How to change UPPERCASE letters to Lowercase in Word:
Option 1:
1. Select or highlight the words or letters.
2. Press Shift and F3 together.
Option 2:
1. Select or highlight the words or letters.
2. Click Format -> Change case -> lowercase
3. Click Ok.
How to convert Lowercase letters to Uppercase in Microsoft Word:
Option 1:
1. Select or highlight the words or letters.
2. Press Shift + F3.
Option 2:
1. Select or highlight the words or letters.
2. Click Format -> Change case -> UPPERCASE
3. Click Ok.
How to capitalized the first letter of the sentence or sentences :
Option 1:
1. Select or highlight the words or letters.
2. Press Shift and F3 together.
Option 2:
1. Select or highlight the words or letters.
2. Click Format -> Change case -> Sentence case
3. Click Ok.
How to change to Uppercase the beginning of each word in a Title:
Option 1:
1. Select or highlight the words or letters.
2. Press Shift + F3.
Option 2:
1. Select or highlight the words or letters.
2. Click Format -> Change case -> Title Case
3. Click Ok.
How to toggle the case of the letters (change uppercase letters to lowercase at the same time changing lowercase to uppercase within the word or words in the sentence):
1. Select or highlight the words or letters.
2. Click Format -> Change case -> tOGGLE cASE
3. Click Ok.
How to change the date format in Excel
Are you annoyed when Excel replaces the dates you enter with numbers, texts, or characters with the format that you don't want? For example, if you type January 2012 in a cell, it will automatically be replaced with 1/1/2012. Another example is when you type 7 Feb, it will automatically be replaced with 2/7/2012. This article will show you how to resolve this problem and display the date format that you want. With the Format Cells function, not only can you format the Numbers but also you can format the Alignment, Font, Border, Patterns, and Protection of the cells in your spreadsheet document. This hub will address the issue of the date entry problem. Some solutions include the use of the Find and Replace command, or even using "magic characters" such as ' but these are not permanent fixes. Below is a better solution that solves the problem from the root cause.
How to change the date format in Excel:
1. Select the cell or cells that you want to format.
2. Click Format -> Cells.
3. Click the Number tab.
4. Select Date under Category.
5. Select the Type of the date format that you want from the list. You can see the Sample date format shown above.
6. Click OK.
Note:
Date formats display date and time serial numbers as date values. Except for items that have an asterisk (*), applied formats do not switch date orders with the Operating System.
How to remove duplicate records in Microsoft Excel
When working on large lists of data records in a spreadsheet, especially entering unrelated words, numbers or characters, these data become duplicated or even entered more than twice. You don't have to worry about duplications because Microsoft Excel has a powerful tool to remove duplicates in a list of records. Don't waste your time to check for duplicates as you enter the values and data. Just type as fast as you can and don't even worry about formatting the table or columns at the beginning, because that should be done after duplicates have been eliminated and final formatting and tabulating of unique records will be done.
I wrote this article because I want people to efficiently and quickly create a table with unique records. I learned from my mistake of wasting too much time of checking and editing everytime I enter a data record. This should be helpful especially when dealing with numerical and alphanumeric characters. I have made the procedure simple so that it is easy to follow.
How to remove duplicate records in Microsoft Excel:
1. Enter all data. Type data records as fast as you can.
2. Click the column header, ie. A, B, C, D, etc, to select all data. Do not put it on the first record.
3. Click Data and either Sort Ascending or Descending.
4. Now you can see duplicates and repeated records.
5. Select the column or cells that you want to remove for duplicates. You only want to display unique records.
6. Click Data on the menu bar.
7. Point to Filter.
8. Click Advanced Filter.
9. On Action, select Filter the list, in-place.
10. On List Range, this will show the cells or column that you highlighted.
11. Put a check mark on Unique Records only.
12. Press OK.
13. Check for duplicates again. There should be no more duplicates at this time.
14. Adjust the Table formatting as necessary.
15. For long lists, you can add another column and transfer the data records.
How to remove green plus + sign in notification bar on your smartphone
You ever experienced those annoying ads on your phone that you never knew where you got it from? Chances are they came with free software apps that you downloaded and installed on your mobile phone device, i.e. your smartphone. These Push Notifications ads are pain in the eyes, they are terrible, everytime I open my cellphone, it shows a virus alert, virus scan, and many ads that are uncalled for and waste of time clearing. Yes, you can always clear them using the Clear button but the best way to get rid of these awful ads is to remove and uninstall the application that is generating these ads. Below is a simple method, an effective way of totally eliminating these push notification ads on your phone:
1. Go to Google Play store.
2. Download Addons Detector by DENPER.
3. Accept and install the app.
4. Once installed, go to Applications and tap on Addons Detector.
5. Tap on Scan, which is the red center button.
6. At the bottom left, it will display the number of Apps and the number of Addons on the bottom right.
7. Press the Addons button, which is the top green button.
8. On Potential addons list, under Filter: Push Notifications, it will list down the apps that might be displaying the unwanted and annoying addons on your smartphone.
9. Tap on Home button.
10. Go to Settings.
11. Applications.
12. Manage Applications.
13. Select the application(s) listed on the Potential addons list.
14. Uninstall.
15. OK.
16. Run the Addons Detector until it says "No applications with addons".
How to remove the hard drive from a dead laptop?
What if your screen is broken by impact or your laptop fall down to the concrete floor. Your monitor may be broken, or dim, or dark, or shattered but there is big possibility that the data and information, your files, folders and documents may still be intact in your hard drive...This article will discuss the instructions that are easy to follow in order to remove the hard drive from your laptop.
Turning an old hard drive into an external storage device
One of the cons of a laptop is when the screen gets damaged or is too dim and dark that you can not see anything. That is what happened to my wife's laptop. The screen had a built-in camera that she used for webcam while on chat and video calling. She also used the laptop to watch streaming videos that made the video card worked so hard. One time, after a long day of chatting and video calling, it was shut down like the usual way but when she started up her laptop on the following morning with the intent of checking her email...POOF!....the screen is totally dark, but the startup sound is still heard with the hard drive light still colored green and the sound of success can still be heard if the password is entered correctly. There were three options that came to my mind to remedy this problem.
First, is to replace the display screen but then the parts and labor is too expensive. Second, is to buy a monitor and plug it to the laptop using a monitor cable and connect it to the display port on the side. This seems to be a reasonable choice but then I will need some space and plus the awkwardness of a black dead screen beside a monitor. Third, is to remove the hard drive and buy a 2.5 inch Serial ATA (SATA) to USB 2.0 HDD enclosure and turn the hard drive as a portable storage device while keeping the original files, folders, media, data, music, photos, videos, and other essentials intact and accessible. The best choice for me turned out to be the third one.
Below I will discuss the step by step procedure of how to remove the hard drive from a dead laptop or one with a dark screen. These instructions are supported with illustrated photos and pictures to understand better for the reader:
1. Disconnect the adapter from the power source.
2. Remove the battery from the laptop.
3. Touch a metal surface to get rid of the static charge in your hands.
4. Turn up the bottom side of the laptop.
5. The hard drive is located inside a lid with an almost square shape. Loosen and remove the two screws.
6. Pull out the cover.
7. Pull out the plastic at the end of the hard drive.
8. Carefully pull the hard drive out, paying attention not to damage the sensitive pin area and connectors.
9. After removing the hard drive from the laptop, handle it with care and carefully place it in a safe, clean, no moisture, no sunlight, no magnetism, no vibration, in an area with no high or low temperatures, while it is not yet inserted and installed in an appropriate hard drive enclosure.
10. Insert and Install the laptop hard drive in a 2.5 inch hard drive enclosure.
How to insert and install a laptop hard drive into a 2.5 inch USB SATA hard drive enclosure:
http://computers-electronics-info.blogspot.ca/2012/12/how-to-insert-and-install-laptop-hard.htmlSaturday, December 15, 2012
How to setup or configure Parental Controls in Windows 7
Windows 7 has some decent family safety features such as the Parental Controls. This helps your kids to learn discipline. Remember what is written in the Bible, "Teach your children right from wrong, and when they are grown they will still do right" (Pro 22:6). "Correct your children, and they will be wise; children out of control disgrace their mothers" (Pro 29:15). By setting up Parental Controls, your children will learn how to manage their time on the computer, inappropriate content from games will be avoided, and they will only have access to programs that you give them permission to. If they learn to abide by these rules then parents will have peace of mind as well as the children. There is nothing worst than letting your child sit on a computer and doing what he wants to do, playing what he wants to play, surfing the internet wherever he/she wants. This is where your responsibility as a father or mother to keep your child on the right path of life. No parent will ever want their children to walk the crooked way of life! Parents want their sons and daughters to grow up as reasonable and respectable citizens.
How to setup or configure Parental Controls in Windows 7: (step by step procedure/instructions)
1. Click Start -> Control Panel -> All Control Panel Items -> Parental Controls.
2. Enter your Administrator password.
3. Click the standard user account (Children).
4. Under Parental Controls, click On, enforce current settings. The Windows Settings icons are now colored.
5. Click Time limits.
Setup the times when you want your child or children to logon and use the computer. Click and drag the hours that you want to allow or block. When the specified time is reached, they will be automatically logged off.
6. Click Games.
You can specify whether your children can play games or not. Control which types of games your child or children can play. You can either Allow or Block games by rating and content types.
7. Click Set game ratings.
You can set game restrictions to game titles that are not appropriate for your child. Even if a game has an allowed rating, you can block it for the type of content it contains. Example, Alcohol and Tobacco Reference, Blood, Cartoon Violence, etc. Titles rated - meanings:
EC - Early Childhood
E - Everyone
E10+ - Everyone 10 years and older
T - Teen, ages 13 years and older
M - Mature, aged 17 years and older
AO - Adults Only, 18 years and older
8. Click Block or allow specific games.
Allow or Block any game installed on the computer. You can control which specific games your child(ren) can and cannot play. You can control each game according to the User Rating Setting (URS) or Always Allow or Always Block. When you choose Always Block, you can see on the Status saying "Can not play".
9. Click Allow and block specific programs.
You can select which programs your child is allowed to run. Put a check on the programs that you allow your child or children to use. Click Ok. Notice the Current Settings of the Children account for Time Limits, Game Ratings, Specific Games, and Program Limits.
10. Click OK to apply your Parental Controls settings for the Children's account.
How to copy or share files or folders with guest user login on Microsoft Windows Network Workgroup
Microsoft Windows Network Workgroup can be a useful tool compared to online storage sites, media and file sharing servers, ftp transfers, or other file transfer solutions over the internet. One advantage is that it is more secure compared to have to find free or freeware or free to try softwares or programs across the web to achieve the same purpose. Another good reason for using Windows home network on Workgroup is that it will save you a lot of headaches in that you are sure you will have (copied) the file on the other computer as opposed to have to try other methods and products and see if it works and if not, find another and try again and it is such a waste of time, effort, energy, and more importantly saving you from harmful viruses, malwares, spywares, and other malicious codes and popups that come with these free programs and not to mention the dreaded and unwanted spam emails you receive from these promoting sites.
Sharing a folder or file through Microsoft Networking and Sharing is simple, easy, and it works...even if you have limited privileges using "guest" as user name on your Windows logon.
Here are the step by step instructions:
1. Ensure the same Workgroup name for both computers. To change or view the Windows Workgroup name, go to Start -> right click My Computer -> Properties -> Computer Name -> OK -> Change -> WORKGROUP
2. Login as Administrator with your Administrator user name on the first computer.
3. Logon as Administrator with Administrator username on the second computer.
4. Check that both computers are on the same Workgroup network. Right click on Start -> Explore -> My Network Places -> Entire Network -> Microsoft Windows Network -> Workgroup
5. Go the shared folder on the computer where you want to copy a file or folder.
6. Select the file/s or folder/s you want to copy and press Ctrl C to copy them.
7. On the other computer (where the guest login is), on the C:\ drive, select a common and accessible folder such as "guest", or "Temp" and paste (Ctrl V) the files or folders.
8. Logoff as Administrator on the computer that has a guest user.
9. Login as guest on the computer mentioned above on step 8.
10. Go to the common folder where you pasted the files or folders on step 7.
How to unlock mobile phone SIM card
How can I make my smartphone or cell phone work in any country that I visit? How to unlock my cell phone or smartphone? These are the common questions that travelers often ask when they go from one country to another and want to use a local mobile network carrier so that they can save money and take advantage of promotional offers. Once your mobile phone is unlocked, it will work with any SIM card. Mobile phone manufacturers include a feature called SIM lock or network lock. This locking feature is used by mobile network providers or carriers to limit your phone's usability to a specific country and mobile network signal providers. This would mean that they can take advantage of offers and contracts so that they will recover their promotional offers (cheap phones or free phones) in exchange of you signing to a contract of usually 3 years and you can select among option based on your preferences, each option with different monthly bill. If your phone is locked, then it would prevent you from breaking the original contract. They lock your phone for safety in case you sign a new contract with a new mobile network provider while being actively under a contract. To avoid contracts and be on the safe side, choose "Pay as you go" or Pre-paid or other similar options. The first important question to take into consideration is:
Is mobile unlocking legal?
Unlocking your mobile phone (smartphones, cellular phones) is absolutely LEGAL.
What is considered illegal?
Unblocking a mobile phone or device is illegal. This is usually in the case where a phone was lost or stolen and was reported by the owner of the phone and consequently blocked by the carrier networks. Unblocking is when you make the phone to work again by crafty means even if it is being actively blocked. Don't attempt to do this. Severe penalty will result.
Is there a catch?
Be careful about your phone's warranty. If you unlock your smartphone or cellullar device, it will make your warranty invalid.
What is the most common way of mobile unlocking?
Entering a mobile unlock code is the easiest way of unlocking your mobile device. This is FREE. Once the unlock code is entered, it allows your mobile phone to work with any network in any country in the world. This unlock code will make your phone to work with any mobile network carrier which then lets you take advantage of savings (no more worries about roaming charges, etc.).
How to unlock my mobile phone: 3 simple steps
1. Obtain your mobile phone information
a. find the brand or model number of your phone (located on either the handset, it's box, or documents)
b. know the network carrier of your phone (this is the one that gives your phone a signal, a network access)
c. find the IMEI code. The International Mobile Equipment Identity (IMEI) code is a unique identifier of all mobile phones manufactured. To find your IMEI code, simply type *#06# or *#6# into your handset , and write down correctly the number on a piece of paper. Also the IMEI number can be found under the battery of your phone.
2. Get the unlock code
This can be done by searching for sites with a list of unlock codes for specific brands and models of phones. Nokia phones are one of the easiest to unlock because of the many websites providing the lists of unlock codes for free. Yes, no charge. You can also get unlock codes by calling a company or internet site for a small fee. Other options are paid services - you pay and they give you your unlock codes or you can bring your phone and they will unlock your phone for you. Some unlock codes are being generated by free downloadable softwares too.
3. Enter unlock code to your mobile phone
For Nokia phones, the code is in the format #pw+1234567890+1# or in the sample format #pw+123456789012345+1# or for other brands of smartphones and cellphones, the code format is *1234*567#. After successfully entering your unlock code, you will get a message saying
"phone restriction off" or similar messages. This step is extremely critical because you have 3 to 5 attempts to input your unlock code for your device. Be careful and check for accuracy. Also make sure you have the correct IMEI code so you will get the correct unlock code.
How to use Smartphone to access internet on Laptop computer
On airports, malls, and other areas where there are free mobile wi-fi hotspots, you can browse and surf the web. But what about when you are in a place where your laptop can find mobile wireless networks but they are all security-enabled networks and all you have is your smartphone? Don't lose hope, you can still browse and surf the internet by setting up your smartphone's internet access to work on your laptop computer. Your smartphone's data and internet access can be configured to provide internet on your laptop. In this way, you can surf the internet using your laptop which provides better and faster experience because of the larger monitor screen, comfortable keyboard, etc. Follow the simple easy steps below to setup your cellphone for your laptop internet access.
Smartphone Setup:
1. Settings
2. Wireless & Networks
3. Tethering & Mobile Hotspot
4. Put a check on Wi-Fi hotspot
Hotspot "device name - MB123-1234" connected
A warning message will pop up saying this application will impact battery life and recommend running the application with the charger connected. A security warning also says that your smartphone device allows you to create a Mobile Hotspot wireless network, which may be accessible by unauthorized users. It is strongly recommeded that you use a strong password to protect your network.
5. Press OK
6. Wi-Fi hotspot settings
7. Configure wi-fi hotspot
- setup Network SSID
- for Security, select WPA2 PSK
- put a strong password
8. Save
Laptop computer setup:
1. Click Start
2. Control Panel
3. Network Connections
4. Double click Wireless network connection
5. Click Refresh network list
6. Choose a wireless network
7. Select the device name (MB123-1234)
8. Press Connect
9. Enter the password that you setup above on smartphone.
10. When successfully connected,
Open internet browser (Internet Explorer, Firefox, Google Chrome, etc.)
Surf the internet...you're good to go!
How to enable port forwarding on your router
A port is a way by which your computer communicate with the internet. Example, an application such as an online game will use the port for incoming or outgoing flow of information. The Hypertext Transfer Protocol (HTTP) is the means by which our computer communicates with other computers in the world and port 80 is the default port of communication. By default, the port number for a web server is port 80.
What is port forwarding?
Port Forwarding will tell the router which computer on your home network to send the data to. Routers assign port numbers to a Service that is associated with a specific Application on your computer. Below is the step by step procedure of how to open ports on your router and how to configure port forwarding.
How to enable port forwarding on your router: (based on a D-Link router)
1. Open a web browser (Internet Explorer or Mozilla Firefox).
2. Type the URL address of the router in your browser. This is usually 192.168.0.1
3. Enter the router's username and password. The default username is "admin". For the password, it generally works by leaving it blank and just pressing Enter.
4. Click on Advanced -> Virtual Server.
5. Check the Enabled button.
6. Give a name for your new virtual server. Example "John Home Web Server".
7. In the Private IP box, enter the IP address of the computer on your local home network where you want the Service (application) to point to.
8. Select "Both" for the Protocol Type.
9. Enter the same port number for Private Port and Public Port.
10. On the Schedule, select "Always".
11. Click Apply.
12. Click Continue.
How to edit, add, or remove Startup programs in Windows
Does your computer take forever to boot up during startup? Your start up programs might be too many that some of them are unnecessary and it is taking too much time to startup. The good news is that you can easily edit these startup program items to speed up your startup time. The procedure is so easy and it takes only a few clicks. Follow the steps below and notice a remarkable improvement on your computer's boot up time. It's gonna startup faster!
How to edit Startup programs in Windows:
1. Click Start.
2. Press Run.
3. Type msconfig.
4. On the System Configuration Utility window, click Startup.
5. Update your start up programs by either checking or unchecking the Startup items. Confirm the start up program by looking at the Command column and check the path where and which program it is pointing.
6. Click Apply.
7. Click Close.
8. Restart computer. If you select this option, the settings for the startup programs will be effective immediately after you restart. If you choose Exit Without Restart, settings will not be effective until you restart your computer.
How to edit startup programs in Windows: (method 2)
1. Click Start button.
2. All Programs.
3. Startup.
4. Open the Startup folder and delete or add shortcuts of start up programs.
How to edit Startup programs in Windows: (method 3)
There are a number of free and paid versions of Windows cleaning, utility, and optimization programs that allow you to edit, add, remove, enable or disable startup programs installed in your computer.
You can also edit startup programs by means of editing the Windows Registry (regedit), but this is not recommended as you can accidentally add or delete sensitive registry entries that can be harmful to Windows performance, or worse, lead to computer malfunction and failure.
Note:
When installing programs in Windows, check the startup preferences, and you can choose whether to start it when Windows starts or simply uncheck the option. Remember, the more startup programs, the slower your computer startup time will be.
How to share contacts and send photos from one smartphone to another using Bluetooth
Bluetooth is a wireless technology that allows you to share or send photos and contact information from one smartphone to another. Although Bluetooth is limited in wireless range to about 30 feet or 10 meters, it provides easy, convenient and hassle free setup without having to use any wires. Bluetooth has many other uses such as hands-free calling, car deck, car video deck, Bluetooth speakers, headsets, GPS, laptop, desktop, notebook computers, TVs, Smart TV, Blu-ray players, Home Theater systems, wireless printing, and many more. Below is a simple, easy to follow, step by step instructions on
How to share contacts and send pictures from one smartphone to another using Bluetooth:
Pair Both Phones
1. Go to Home -> Settings -> Wireless and Network -> Turn on Bluetooth. Do the same steps for the other phone.
2. At this point, both phones should have their Bluetooth connectivity turned on. In Bluetooth Settings, Scan for devices.
3. Select the device you want to pair (which is the other phone).
4. The Pairing process will send a numeric password or code to the other device to be paired with.
5. The other smartphone will be asked for Confirmation, if the password or code is the same from the one sent to the one received, the other phone is ready to Accept the device. Once the Accept button is pressed, both smartphones should now be paired. In some devices, when the pairing procedure is successful, it should indicate Paired, in other devices, it says "Paired but not connected", but in both cases, it should work.
Sharing or sending pictures or photos
1. Go to Home -> Applications
2. Press Camera
3. Select a photo or picture to share or send
4. You can tap (slightly press) the photo or press the Options button
5. Select Share
6. Share picture via -> Bluetooth
7. Select the paired device
8. Authorization request is sent
9. Press Accept button
10. To confirm if the file is received and transfer operation is a success, go to Home -> Applications
11. Files -> bluetooth folder
12. Search for the picture/photo.
Sharing or sending contact information
1. Go to Contacts
2. Select a contact
3. Press and hold the contact
4. Scroll down the menu to Send namecard via
5. Select Bluetooth
6. Press the Paired smartphone to Send to the selected device
7. On the other phone, a Notification is sent. It will ask for Confirmation and shows the Accept button
8. Once it is accepted and sent successfully, a notification is sent again both the sending and receiving device
9. To confirm that you really received the file, go to Home -> Applications
10. Files -> Internal phone storage
11. Scroll to Bluetooth folder
12. Find the name card.
How to take ownership, control, and have access to a file or folder(s) from an old hard drive
Plugging the old hard drive to the USB port of your computer to browse files
After installing the old laptop hard drive to the 2.5 inch HDD SATA to USB 2.0 Hard Drive Enclosure, it is now time to plug it into the USB port of your computer (desktop or laptop) in order to test that the data, music, video, media, and other essential files are intact and in good condition.
If you used a Plug n Play Hard Drive Enclosure and you are plugging it into a computer with Windows XP or higher, you don't have to do anything (no driver installation or restarting). After plugging in your Hard Drive that is now inserted into the Hard Drive Enclosure, your computer should display a message "Found new hardware" in the task bar.
Next, is to click
Start --> My Computer
and it should show you a new drive with a new drive letter. Explore and browse the files and folders and in case you can not access or even view these files, and a message saying
"Access is denied",
you need to get Permissions in Administrator level. To do this, do the following step by step procedure (based on Windows XP Home edition operating system):
1. Restart your computer in Safe Mode.
2. Press repeatedly F8 during the restart and select Safe Mode using the arrow key.
3. Log on as an Administrator.
4. A message will say "Windows is running in safe mode.", "To proceed to work in safe mode, click Yes."
5. Browse to the folder that you want to have access to.
6. Right-click the folder or folders that you want to have access to, have control, and take ownership.
7. Click Properties.
8. Click the Security tab.
9. Click Advanced.
10. Click the Owner tab.
11. In the Name list, click Administrator, or click the Administrators group.
12. Click OK.
The Permissions for Administrators will enable you to either Allow or Deny the following privileges:
- Full Control
- Modify
- Read and Execute
- List folder contents
- Read
- Write
- Special Permissions
13. Click the Start button.
14. Restart your computer in Normal Mode.
Adding a new user account and giving access Permissions
If you want to add a certain user account and give a certain access level to a user (for example "guest"), follow these steps:
1. Click Add.
2. In the Enter the object names to select (examples) list, type the user (in this case, type "guest")
3. Click OK.
4. In the Group or user names list, click the "guest" account.
5. Click to select the check boxes of the Permissions that you want to assign to "guest" user.
- Full Control
- Modify
- Read and Execute
- List folder contents
- Read
- Write
- Special Permissions
6. After you are finished assigning user Permissions for "guest", click OK.
7. Restart your computer in Normal Mode.
Changing the Permissions for access level for an existing user account
In order to change the permissions on a file or folder or folders for an existing user account, follow these steps:
1. In the Group or user names list, click the Name of the user account.
2. Click to select the check boxes of the Permissions that you want to assign to the user.
- Full Control
- Modify
- Read and Execute
- List folder contents
- Read
- Write
- Special Permissions
3. After you are finished assigning user Permissions for the selected user, click OK.
4. Restart your computer in Normal Mode.
Friday, December 14, 2012
How to upload photos and videos from digital camera to laptop or desktop computer
Uploading pictures or photos/images and videos to your laptop or desktop computer is generally similar regardless of the name, brand or model of your digital camera. The procedure is quite simple, think of it like this: imagine your digital camera as a grocery bag with meat and vegetables; imagine your laptop or desktop computer as your refrigerator with freezer and vegetable rack. Think of the meat as the photos and the vegetables as videos. Before you can transfer (UPLOAD) the contents of your grocery bag (DIGITAL CAMERA), there should be a place/compartment/container (FOLDERS) - the freezer (PHOTOS FOLDER) for the meat (PHOTOS) and the vegetable rack (VIDEOS FOLDER) for the vegetables (VIDEOS) in your fridge (COMPUTER) where you will put your groceries.
The following steps below explain in simple to follow instructions on how to upload pictures and videos from a Canon SD1100 digital camera to your computer. Note that in similar and other models of Canon digital cameras or other brands and models of digital cameras, these instructions (steps) on this procedure will generally be applicable.
Step by step procedure how to upload photos and videos to your laptop/desktop computer (Windows Vista):
1. Go to My Documents.
2. Right click on the empty white space --> New --> Folder --> name it starting with the date and a short description. (Example: 2010-12-25-Christmas in Toronto).
3. Make sure the digital camera is OFF.
4. Move down the camera switch to TRIANGLE ENCLOSED WITH RECTANGLE (View Mode).
5. Open the A/V OUT DIGITAL and insert the smaller end of the TRANSFER CABLE.
6. Insert the bigger end of the TRANSFER CABLE to the USB port on the laptop or desktop computer.
7. Turn ON the camera.
8. Double click Removable Storage.
9. Double click DCIM.
10. Double click 100CANON.
11. Click on the first picture you want to upload.
12. Press and hold down steadily the SHIFT Key while clicking the last photo you want to upload.
13. With the pictures selected, press and hold down steadily the CONTROL (CTRL) Key while pressing C to copy the photos.
14. Double click the FOLDER you created on step 2 --> 2010-12-25-Christmas in Toronto.
15. Press and hold down steadily the CONTROL (CTRL) Key while pressing V to paste the photos to the FOLDER you created on step 2 --> 2010-12-25-Christmas in Toronto.
16. Remove the TRANSFER CABLE from the USB port.
17. Turn OFF the digital camera.
18. Pull out TRANSFER CABLE from the A/V OUT DIGITAL.
Note:
The instructions above copies pictures. To copy videos, do the same steps/instructions/procedures but this time, select VIDEOS that you want to copy or upload to your laptop/desktop computer.
-----------------------------------------------------------------------
Step by step procedure how to upload photos and videos to your laptop/desktop computer (Windows XP):
1. Go to My Documents.
2. Right click on the empty white space --> New --> Folder --> name it starting with the date and a short description. (Example: 2010-12-25-Christmas in Toronto).
3. Make sure the digital camera is OFF.
4. Move down the camera switch to TRIANGLE ENCLOSED WITH RECTANGLE (View Mode).
5. Open the A/V OUT DIGITAL and insert the smaller end of the TRANSFER CABLE.
6. Insert the bigger end of the TRANSFER CABLE to the USB port on the laptop or desktop computer.
7. Turn ON the camera.
8. Under Canon PowerShot SD1100 IS, Select Microsoft Scanner and Camera Wizard --> Press OK.
9. Under Scanner and Camera Wizard --> Click Next.
10. Select pictures you want to upload to your computer.
11. Type a name for this group of pictures.
12. Under Choose a place to save this group of pictures, Click Browse.
13. Find and click the FOLDER you created on step 2 --> 2010-12-25-Christmas in Toronto --> Click next.
14. Under What do you want to do, select "Nothing. I'm finished working with these pictures.
15. Click Next --> then press Finish.
16. Remove the TRANSFER CABLE from the USB port.
17. Turn OFF the digital camera.
18. Pull out TRANSFER CABLE from the A/V OUT DIGITAL.
Note:
The instructions above copies pictures. To copy videos, do the same steps/instructions/procedures but this time, select VIDEOS that you want to copy or upload to your laptop/desktop computer.
Shortcut keys for Windows, Windows Explorer, Word, Internet Explorer, Firefox, & Google Chrome
If you can do something fast and you know how to do it faster, why not do it? Yes, the mouse is fine and the touchpad is doing great but sometimes your fingers get stressed by using them over and over again for continuous period of time that you want to get rest and relax. By knowing keyboard shortcuts, there is an alternate way of achieving the same results and often faster and reliable. It buys you some time to relax the finger muscles you have been using and use another finger or group of muscles and bones, therefore a balance is achieved, giving you comfort and relieving some stress.
For some people, keyboard shortcuts are very convenient and they do work faster, save time, and do more. Anyways, my objective is to provide help to people who wants to know and learn some helpful keyboard shortcut keys for their benefit and convenience. There are three groups of keyboard shortcuts here: Windows and Windows Explorer, Microsoft Word, and Browser shortcuts (this applies to Internet Explorer, Mozilla Firefox, and Google Chrome).
Important Note:
When pressing more than one key, the + key is not part of the shortcut. For example, CTRL + ESC means that you have to press the CTRL and ESC keys only. The + key is not part part of the shortcut, therefore, it is NOT to be pressed.
Windows and Windows Explorer shortcut keys
Function keys keyboard shortcuts:
F1 --- Help
F2 --- Rename
F3 --- Find
F4 --- Go to a different folder
F5 --- Refresh
F6 --- Move among panes
F10 --- Menu bar options
Single key keyboard shortcuts:
ESC --- Cancel
TAB --- Move next
ENTER --- Go (same effect as click)
ALT --- Works in combination with an underlined letter
SHIFT --- Bypass automatic run of CD, DVD
SPACEBAR --- Enter, Toggle, Select
INSERT --- Insert an object, letter, word, or item without replacing
DELETE --- Delete an item and put in Recycle Bin
BACKSPACE --- Go Back, Switch to the parent folder
SHIFT combination keyboard shortcuts:
SHIFT+TAB --- Move previous
SHIFT+DELETE --- Delete item permanently (this does not go to Recycle Bin)
SHIFT+F10 --- Context menu for the selected item (same effect as Right-click)
SHIFT+Windows Logo+M --- Undo minimize all
ALT combination keyboard shortcuts:
ALT+TAB --- Switch between open programs
ALT+F4 --- Quit program, Close window
ALT+DOWN ARROW --- Drop-down list
ALT+ENTER --- Open properties of selected object
ALT+SPACE --- Display system menu
CTRL combination keyboard shortcuts:
CTRL+ESC --- Open Start menu
CTRL+ENTER --- Maximize window, Full screen
CTRL+Z --- Undo
CTRL+C --- Copy
CTRL+V --- Paste
CTRL+X --- Cut
CTRL+A --- Select all
CTRL+B --- Bold
CTRL+U --- Underline
CTRL+I --- Italic
Windows Logo key combination keyboard shortcuts:
Windows Logo --- Start menu
Windows Logo+F1 --- Windows Help and Support Center
Windows Logo+E --- Windows Explorer
Windows Logo+F --- Find files or folders (Search)
Windows Logo+L --- Lock the computer
Windows Logo+L --- Log off Windows
Windows Logo+R --- Run
Windows Logo+M --- Minimize all
Windows Logo+D --- Minimizes all open windows and displays the desktop
Windows Logo+TAB --- Cycle taskbar
Windows Logo+Break --- System Properties
Three-key combination keyboard shortcuts:
CTRL+SHIFT+ESC --- Opens Windows Task Manager
CTRL+ALT+DEL --- Windows Task Manager, Logoff, Lock, Restart, Shutdown
-----------------------------------
Microsoft Word keyboard shortcut keys
Function key shortcut keys:
F1 --- Help
F2 --- Edit, Move Text
F4 --- Redo or Repeat
F8 --- Begin highlight, Extend Selection
F9 --- Update Fields
F10 --- Menu
F11 --- Next Field
F12 --- Save As
Single shortcut keys:
ESC --- Cancel
END --- End of Line
TAB --- Next Cell
INSERT --- Overwrite, Overtype
HOME --- Start of Line
DELETE --- Erase, Clear, Delete
CTRL shortcut keys: File, Page
Save --- CTRL+S
New Document --- CTRL+N
Open Document --- CTRL+O
Print --- CTRL+P
Print Preview --- CTRL+F2
Page Break --- CTRL+ENTER
CTRL shortcut keys: Word formatting, Picture, Number, Characters
Copy --- CTRL+C
Paste --- CTRL+V
Cut --- CTRL+X
Undo --- CTRL+Z
Redo or Repeat -- CTRL+Y
Subscript --- CTRL+ =
Superscript --- CTRL+SHIFT+ =
CTRL shortcut keys: Formatting, Paragraph, Sentence
Left --- CTRL+L
Right --- CTRL+R
Center --- CTRL+E
Justify --- CTRL+J
Indent --- CTRL+M
Bold --- CTRL+B
Italic --- CTRL+I
Underline --- CTRL+U
CTRL shortcut keys: Find and Replace (Searching words)
Find --- CTRL+F
Replace --- CTRL+H
CTRL shortcut keys: Selection, Highlighting
Select All --- CTRL+A
Highlight until the Start of Document --- CTRL+SHIFT+HOME
Highlight until End of document --- CTRL+SHIFT+END
CTRL shortcut keys: Linking, Locking
Hyperlink --- CTRL+K
Unlink Fields --- CTRL+6
Unlock Fields --- CTRL+4
CTRL shortcut keys: Cursor, Document
Word Left --- CTRL+LEFT
Word Right --- CTRL+RIGHT
Browse Next --- CTRL+PAGE DOWN
Browse Previous --- CTRL+PAGE UP
End of Document --- CTRL+END
Start of Document --- CTRL+HOME
SHIFT shortcut keys:
Highlight Up --- SHIFT+UP
Highlight Page Up --- SHIFT+PAGE UP
Highlight Down --- SHIFT+DOWN
Highlight Page Down --- SHIFT+PAGE DOWN
Highlight until End of Line --- SHIFT+END
Highlight until the Start of Line --- SHIFT+HOME
Change Case --- SHIFT+F3
Previous Cell --- SHIFT+TAB
Previous Field --- SHIFT+F11
Repeat Find --- SHIFT+F4
Thesaurus --- SHIFT+F7
Tool --- SHIFT+F1
ALT shortcut keys:
Close or Exit --- ALT+F4
Start of Row --- ALT+HOME
End of Row --- ALT+END
End of Column --- ALT+PAGE DOWN
Previous Object --- ALT+UP
Redo --- ALT+SHIFT+BACKSPACE
Dictionary --- ALT+SHIFT+F7
-----------------------------------
Browser Keyboard shortcuts for Internet Explorer, Mozilla Firefox, and Google Chrome
Function keys shortcuts:
F3 --- Find
F5 --- Refresh page
F11 --- Full-screen, Regular view
F10 --- Menu
Single key shortcuts:
ESC --- Stop downloading
BACKSPACE --- Go Back, Undo, Return
ALT keys shortcuts:
ALT + Left Arrow --- Back
ALT + Right Arrow --- Forward
ALT + HOME --- Homepage
CTRL keys shortcuts:
CTRL + + --- Zoom In
CTRL + - --- Zoom Out
CTRL+ 0 --- Zoom Reset
CTRL + S --- Save, Save Page as
CTRL + O --- Open file
CTRL + T --- New tab
CTRL + N --- New Window
CTRL + F --- Find within the page
CTRL + P --- Print
CTRL + R --- Reload page
CTRL + I --- Open Favorites
CTRL + D --- Add to Favorites, Add to Bookmarks
CTRL + B --- Open Favorites, Organize Favorites folder, Open Bookmarks
CTRL + W --- Close tab
CTRL + TAB --- Switch tabs
SHIFT + ENTER --- Open link in new window (must be selected by TAB first)
Ipad and Ipad 2: Comparison, Differences, Similarities, and Technical Specifications
Ipad 2 is the latest and newest version of the Ipad tablet computer which was released on April 2010. With the new Ipad 2 released on March 2011, its OS is 4.3, Processor is A5, dual core, with front and rear camera, screen rotation in all four directions, it is 33% thinner, 15% lighter, with lots of improved, new stuff, cooler and more enjoyable features than the previous Ipad release. Ipad 2 is simply a prettier gadget to surf the web, read e-books, watch videos, record videos, take photos, play games, video-calling, locate an address, listen to music, and many more fun things for you to enjoy, explore and take advantage of.
Ipad vs. Ipad 2 Comparison and Differences in Technical Specifications:
Operating system (OS):
Ipad: OS 4.2.1
Ipad 2: OS 4.3
*** Ipad 2 has newer OS version
Dimensions:
Height:
Ipad: 9.56 inch
Ipad 2: 9.5 inch
*** Ipad 2 is shorter
Length:
Ipad: 7.47 inch
Ipad 2: 7.31 inch
*** Ipad 2 is smaller in length
Depth:
Ipad: 0.52 inch
Ipad 2: 0.34 inch
*** Ipad 2 size is thinner
Weight:
Ipad: 1.5 lbs (Wi-Fi), 1.6 lbs(3G)
Ipad 2: 1.33 lbs (Wi-Fi) 1.35 lbs (GSM)
*** Ipad 2 is lighter in both Wifi and GSM models
Edge Finish:
*** iPad 2 has smoother edges and sleeker finish
Processor:
Ipad: 1 GHz Apple A4 (single core)
Ipad 2: 1.08 GHz Apple A5 (dual core)
*** Ipad 2 has more powerful and faster processor for running multiple applications
Random Access Memory (RAM):
iPad: 256 MB
iPad2: 512 MB
*** iPAD2 has bigger RAM
Camera:
iPAD: none
iPAD 2:
Front Camera - VGA-quality still camera, video recording (30 frames per second with audio)
Rear Camera - 5x digital zoom still camera, video recording, HD (720p), 30 frames per second with audio
*** iPAD 2 has both front and rear cameras
Video out:
Ipad: none
Ipad 2: HDMI (w/ accessory included)
*** Ipad 2 has an HDMI video out
Audio playback:
Ipad: none
Ipad2: Dolby Digital 5.1 surround sound pass-through (with Apple Digital AV Adapter)
*** Ipad2 has Dolby Digital 5.1 surround sound capability
3G Radio:
ipad: no
ipad2: CDMA, EV-DO
*** ipad2 has 3G Radio (CDMA)
Gyroscope:
IPAD: none
IPAD 2: Yes
*** IPAD 2 has a gyroscope
Price (Wi-Fi):
iPad: starts at $399
ipad 2: starts at $499
*** ipad 2 is more expensive
Price (3G):
Ipad: starting at $529
Ipad2: starting at $629
*** Ipad is cheaper
iPad and iPad 2 Similarities in Specs:
The following features are present and the same in both the IPAD and IPAD 2 as well:
Battery Life and Power:
10 hours continous use (25-watt-hr rechargeable lithium-polymer)
Battery Life and Power:
30 days (1 month before recharging) stand-by mode
Battery Charging:
via power adapter or USB to computer system
Display size:
9.7 inch diagonal
Display Resolution:
1024 x 768 (with LED Backlighting)
Wi-Fi access:
802.11 a/b/g/n
3G Radio (GSM):
UMTS/HSDPA/GSMEDGE
Bluetooth:
2.1 + EDR technology
GPS:
3G
User Storage capacity:
16 GB, 32 GB, 64 GB flash drive
Sensors:
Ambient Light, Accelerometer sensor
Location/GeoLocation:
Wi-Fi, Digital Compass (Magnetometer)
Wi-Fi, Digital compass, Assisted GPS, Cellular (WiFi+3G Model)
Language support:
multi-language, international languages supported
Dictionary support:
multi-language, international languages
Operating temperature:
32° to 95° F (0° to 35° C)
Maximum operating altitude:
10,000 feet (3000 m)
Input and output:
* 30-pin dock connector port
* 3.5-mm stereo headphone minijack
* Built-in speaker
* Microphone (Mic)
* Micro-SIM card tray (Wi-Fi + 3G model)
System Requirements:
Mac OS:
* Mac computer with USB 2.0 port
* Mac OS X v10.5.8 or later
* iTunes 9.0, iTunes 10.2 or later
* iTunes Store account
* Internet access
Windows:
* PC with USB 2.0 port
* Windows 7; Windows Vista; Windows XP Home; Windows XP Professional with Service Pack 3 or later
* iTunes 10.2 or later recommended
* iTunes Store account
* Internet access
Thursday, December 13, 2012
Byte: a basic unit of data storage capacity in consumer electronics, devices, and products
Ever wondered what is MB, GB, TB on your cellphones, Ipods, MP4s, Iphones, Ipads, Blackberry phones, laptops, handhelds, USB pen drives, digital cameras, videocams, camcorders, desktop computers, hard drives, PlayStations, PS2, PS3, Xbox, Xbox 360, Wii, PSP, and so on... in those electronic devices, products , gadgets, and gizmos?
A byte is a unit of data storage capacity. The size of a byte depends on the hardware used for a certain device or product. One byte is used to represent or store one character and is generally equivalent to 8 bits. One bit (binary digit) can only have one value of either 0 or 1.
A character (letter, number, punctuation mark, etc.) like 'c' or '5' or '/' or '?' or space is equal to 1 byte.
A useful rule of thumb is One Thousand characters equals 1 KB.
The Binary Table:
1 byte = 8 bits = 1 character
1 Kilobyte (KB) = 1024 bytes
1 Megabyte (MB) = 1024 KB
1 Gigabyte (GB) = 1024 MB
1 Terabyte (TB) = 1024 GB
1 Petabyte (PB) = 1024 TB
1 Exabyte (EB) = 1024 PB
Tuesday, December 11, 2012
Uses of AIRPLAY, BLUETOOTH & WI-FI
What is AIRPLAY?
AirPlay is a technology developed by Apple company that is used to wirelessly stream media such as pictures, music, and video. Airplay is used mainly between Apple devices such as iPad, iPhone, iPod, and iPod Touch but the audio streaming of some non-Apple devices also uses Airplay. Although Airplay works on the traditional wired Ethernet connection, the main goal of Airplay is for wireless streaming (via Wi-Fi) of media so that it is available to any room in the house at any time. When you use AirPlay-enabled speakers with graphical displays, the AirPlay wireless technology also streams the information about your music such as the title of the song, the artist, the name of the album, and other related information directly to your speaker's display.
What is BLUETOOTH?
Bluetooth is an open (to all manufacturers, not only Apple) wireless technology that is used to transfer data or stream media like audio, photos, and contact information from one Bluetooth enabled device to another. Bluetooth was originally designed for portable equipment and mobile devices. Without the need of a Wifi network, Bluetooth is a wireless networking technology that uses low-frequency signals to transmit and receive. Main uses and applications of Bluetooth are with smartphones, tablet computers, notebook, laptop, desktop computers, Blu-ray players, AV receivers, home theater systems, wireless printing, hands-free calling, headsets with Bluetooth, Car deck, In-Dash Car Video Deck, GPS receivers, and many more.
Key advantages of Bluetooth:
- Bluetooth works without a Wi-Fi network
- provides better and flexible compatibility between devices and operating systems
- good audio quality
- simplicity of setup and installation
- reasonable range of 30 feet or 10 meters
- reasonably affordable prices
- no more messy wires to connect
Difference between Bluetooth compatible and Bluetooth-enabled
Bluetooth Compatible or sometimes called "Bluetooth ready" means that the device supports Bluetooth wireless technology and uses an external (via USB) Bluetooth adapter or dongle. Bluetooth Enabled or "built-in Bluetooth" means the device has a Bluetooth adapter already built-in within the inside of the device and does not need an external USB adapter or USB dongle.
What is WI-FI?
Wi-fi networking uses a wireless router to connect wifi devices such as computers, printers, smartphones, blu-ray players, modern TVs (HDTV, plasma TV, LED TV, 3D TV, Smart TV), video game consoles, digital audio players, and other Wi-Fi ready and Wifi-enabled or Wifi built-in devices. These wifi devices can be setup in their Wi-Fi settings to enable them to connect to the wi-fi router access point or hotspot. A wireless router allows connection to the Internet and is usually effective to within 100 feet (30 meters) range. Wi-fi is used in wireless local area networks (WLAN). Wi-Fi is the wireless replacement alternative to the traditional wired Ethernet network which uses Ethernet cables. Using Wi-fi, a smartphone does not need the cell phone provider's 2G, 3G, or 4G networks to send and receive email text messages, voice messages, photos and pictures, audio and music files, videos, and other file transfer services.
WiFi Ready vs. WiFi Built-in
Wi-Fi ready means the device supports wireless Wi-Fi connection but no wifi adapter is integrated to the device. An external adapter has to be purchased separately and has to be plugged in to the device using the USB port. Wi-Fi built-in means that the device already has an adapter or a transmitter/receiver that is installed inside the device. Both Wi-Fi ready and Wifi built-in devices are capable of streaming contents from the internet or from the home network devices and servers.
Popular and major uses of Wi-Fi:
- connecting bluray players, home theatre systems, TVs, computers to the home wi-fi network
- wirelessly transfer, send, share, stream media files, movies, music, videos, photos
- stream audio to any speaker, anywhere, any time within your home, house, or small office
- sync or wireless synchronization of music, photo, video, movie libraries and other files (no more wires to connect and no more plugging of the device to the USB port)
- wireless printing of documents
- using wi-fi, a smartphone can be used as a modem (tethering) for connecting your laptop computer to the internet
- using wifi, a smartphone can be used as a remote control
- many more applications...
Sunday, December 9, 2012
How to insert and install a laptop hard drive into a 2.5 inch USB SATA hard drive enclosure
An external hard drive enclosure is cheaper when you order online or when you buy it at factory direct computer liquidator stores. When you buy the HDD Enclosure in retail stores like Future Shop, Best Buy, etc., the price is over 3 times and unbelievably expensive.
A typical 2.5 inch Serial ATA (SATA) hard drive enclosure package includes the Aluminum Case, USB 2.0 Y-cable, User's manual, Installation screws, Carrying pouch, and a Screwdriver. The Aluminum material casing ensures protection from vibration and overheating. USB 2.0 technology supports fast transfer speeds of up to 480 Mbps. For Windows XP systems and higher, no driver installation is required and Plug n Play feature is applicable. This device is Hot-swappable which means a Plug & Play without rebooting or restarting your computer machine. The USB Y-Cable ensures support of USB 1.1 and the second cable is for drawing additional power from the computer in case it is needed by the hard drive. The User's manual includes installation instructions illustrated with photos and pictures step by step easy to follow procedure. The compact design of the enclosure makes it easy to carry with you in your pocket or bag with the included carrying pouch providing extra protection and convenience. The installation screws and screwdriver makes you insert and install the laptop hard drive into the external enclosure a breeze.
After you successfully insert and install the old hard drive (from the old dead laptop) into the external hard drive enclosure, it should provide you a portable, convenient, lightweight, fast and high performance, handy and efficient storage for your multimedia files such as music, photos, videos, and other essential files and data.
Below, I will discuss the simple to follow instructions and step by step procedure of How to insert and install a laptop hard drive in a 2.5 inch USB SATA hard drive enclosure. Also, photos and pictures provided should benefit the reader making an easy to understand guide and a relaxing, painless learning process:
1. Before starting, touch a metal surface to get rid of static in your hands.
2. Pull the connector out of the HDD enclosure.
3. Carefully insert the power and data connectors to the hard drive.
4. Slowly insert the Laptop hard drive into the HDD external enclosure making sure that the vibration pads are positioned at the bottom.
5. Mount the two screws to secure the connector.
6. Plug the smaller end of the USB Cable to the hard drive.
7. Plug the other end of the USB Cable to the USB Port in your computer. Notice that it should light up when connected.
After connecting your hard drive with the installed enclosure to your computer, it is now time to check for the data files and folders inside it. When you try to explore and browse the contents of the hard drive, you may NOT see and view the files right away and may see a message "This folder is not accessible" or "Access is denied" or similar messages, if this happens, then click this link below to remedy and solve the problem.
How to take ownership, control, and have access to a file or folder(s) from an old hard drive
http://computers-electronics-info.blogspot.ca/2012/12/how-to-take-ownership-control-and-have.html
PICTURES:

01. Touch a metal object or surface to drain the static out of your hands.
02. A typical 2.5 inch SATA External Hard Drive enclosure package.
03. Pull out the connector.
04. Take out the connector carefully.
05. Insert the power and data connectors to the hard drive.
06. The connector fully inserted.
07. Insert the hard drive into the enclosure - black vibration pads to the bottom.
07a. Tighten loose and protruding screws if there are.
08. Use a screw driver to help you insert in tight areas.
09. The 2.5 inch laptop hard drive fully inserted into the external enclosure.
10. Using the screwdriver provided, mount and tighten the two screws on the side of the enclosure.
11. Plug the smaller end of the USB Cable to the hard drive.
12. Smaller end of the USB cable connected to the hard drive.
13. Insert the bigger end of the USB Cable to the USB Port of your computer.
14. The hard drive connected to the USB port of the computer.
How to clean Laptop fan
How to clean laptop computer cooling fan?
Do you hear that annoying sound of your laptop computer's fan when it is running fast, hard, and noisy especially when you are playing online videos such as youtube videos or when playing video games? Does your laptop touchpad, keys, and keyboard heat up? Does the bottom or underneath of your laptop is abnormally hot and noisy? If the answer to any or all of these questions is yes, chances are that your laptop computer cooling fan and air suction, exhaust, and passage grill or screen are dirty. Below I will describe clearly and logically in an easy and simple to follow instructions the step by step procedure how to carefully and safely clean your laptop cooling system.
How to clean laptop computer cooling fan and cooling system:
1. Shutdown and turn the power off your laptop. Remove the charger chord and the battery.
2. Close the lid (screen) of your laptop.
3. Turn your laptop upside down so that the bottom part is now facing you.
4. With an appropriate screwdriver, loosen the screw of the cover where your cooling fan is located.
Fig.1
5. Unscrew the cooling system fastening screws. In this Asus 2004 model laptop, there are 4 screws.
Fig. 2.
6. Unscrew the fan securing screws. These are 3 screws secured to the fan housing assembly.
Fig. 3.
7. Lift the fan from the fan housing. Be careful not to pull the wires connecting the fan to the laptop.
Fig. 4.
8. Remove the cooling fan housing. Clean inside and outside of the housing.
Fig. 5.
9. Clean using smooth lint free cloth, don't use corrosive cleaning solutions. Moisten the cloth with little amount of water.
Fig. 6.
10. Clean the air inlet grille. This is the most important part to clean as this is where the air passes through the small grill openings. This is the most dirty area where the dust and dust bunnies accumulate, blocking the air flow and causing your laptop to overheat because cooling air passage is restricted.
Fig. 7.
11. Clean the cooling fan blades and surrounding areas of the fan.
12. After cleaning is done, assemble and screw the fan to the fan housing. Screw the fan housing and assembly to the bottom of the laptop. Finally screw the cover underneath the laptop.
13. Replace the laptop battery and plug the charger.
14. Test the laptop. It should now be quiet and cool in operation.
 |
| 1-Upside down. |
 |
| 2-Unscrew the cooling system fastening screws. |
 |
| 3-Unscrew the fan securing screws. |
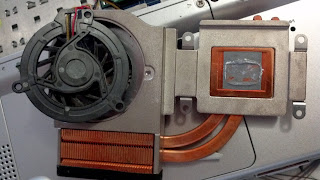 |
| 4-Lift the fan from from the fan housing. |
 |
| 5-Remove the cooling fan housing. |
 |
| 6-Cooling fan housing and cooling assembly to be cleaned. |
 |
| 7-Air inlet grill to be cleaned. |
Saturday, December 8, 2012
How to setup & configure a fast, secure, organized and efficient home network
A seemingly complicated business enterprise model network may have lots of interconnected devices but it is built upon a simple basic configuration.
The setup and configuration below is based on a home network of 5 components:
1. D-LINK DI-524 (802.11g/2.4GHz Wireless Router) --------------------> Gateway
2. Dell Desktop (Microsoft Windows XP Home Edition Service Pack 2) ---> File Server
3. Asus Laptop (Microsoft Windows XP Home Edition Service Pack 2) ----> Mobile PC
4. Toshiba Laptop (Microsoft Windows Vista Home Premium) -------------> Mobile PC
5. Cables (Ethernet, Coaxial) ----------------------------------------> Connectors & for Data Transfer
In the simple basic home network above, the following are achieved:
SECURITY
* broadcasting of SSID is disabled (with the wireless setting for the Access Point SSID Broadcast set to "Disabled", a nearby neighbour is prevented from discovering your network)
* WPA-PSK Security setting (new models of routers have WPA2 security type and AES encryption type which are the latest technology for wireless security)
* strong hard-to-guess, carefully chosen passwords are essential for better secured networks
* DHCP IP Addresses are limited to two (knowing beforehand that there are only two laptop computers and setting the Starting and Ending IP addresses so that the router is only allowed to supply 2 IP Addressess, thereby lessening the probability of access from potential sniffers to your wireless home network)
SPEED, MOBILITY, EFFICIENCY
* Speed is achieved because the router doesn't have to choose dynamically from 100 IP Addresses (under DHCP Server, the D-Link Router has by default Starting IP Address 192.168.0.100 and the Ending IP Address 192.168.0.199, by controlling these limits, it can only be restricted to give access to two client computers)
* Mobility is achieved by setting the two laptops with Dynamic (DHCP) IP Addresses instead of Static IP Addresses [for a network administrator in a business enterprise network, setting the mobile laptops with DHCP IP Addresses instead of Static IP Addresses has the advantage of easy management and maintenance while offering the flexibility of the laptop users to access a different subnet within the business network and thereby minimizing downtime for administrator setup in case the users move from one department to another department]
* Efficiency and Organization is achieved by setting the File Server with a Static IP Address so that its address is fixed, readily available to everyone on the network to be easily accessed
-------
How to disable SSID Broadcast of your Home Network
1. Open an Internet Explorer browser
2. Type in the address bar http://192.168.0.1 and press Enter
3. Type the user name and password for the admin
Fig. 1
4. Click the "Wireless" button on the left
5. Under Wireless Settings, SSID Broadcast: select Disabled
6. Click Apply
Fig. 2
-------
How to manually connect to a wireless network with SSID Broadcast disabled (Windows Vista)
1. Click Start ---> Control Panel
2. Under Network and Internet, click "View network status and tasks"
fig
3. Under Tasks, click "Set up a connection or network"
fig
4. Under Choose a connection option, click "Manually connect to a wireless network"
5. Click Next
fig
6. Under Enter information for the wireless network you want to add,
Network name: Enter the Name of the Network you want to connect to
Security type: Select WPA2-Personal (this is the latest technology in wireless security, most secure system)
Encryption type: Select AES
Security key/Passphrase: Enter the network password
Put a Check: Start this connection automatically
Put a Check: Connect even if the network is not broadcasting (this is important! Don't forget to tick this)
7. Click Next
fig
8. Under Successfully added "NameOfNetwork", Click Close
fig
-------
How to manually connect to a wireless network with SSID Broadcast disabled (Windows XP)
1. Click Start ---> Control Panel
2. Double click Network Connections
fig
3. Under LAN or High-Speed Internet, click "Wireless Network Connection"
fig
4. On the left, under Network Tasks, click "Change settings of this connection"
fig
5. Under Wireless Network Connection Properties, click Wireless Networks tab
fig
6. Under Preferred Networks, click Add
fig
7. Under Wireless Network Properties on the "Association" tab
Network name (SSID): Enter the name of the Network you want to connect to
Network authentication: select WPA-PSK (if WPA2 is available in the drop-down list, select WPA2, this is the latest improvement on wireless network security system, hence most secure option)
Data encryption: select AES
Network key: Enter the wireless network password
Confirm network key: Reenter the wireless network password
fig
8. On the Connection tab, under Automatic connection, make sure
"Connect when this network is in range" is checked
9. Click Ok
fig
10. Under Preferred Networks, check to see that the Network (Automatic) has been added in the box
11. Click Ok
fig
-------
How to set the Security Type and Password Protect your Home Network
1. Open an Internet Explorer browser
2. Type in the address bar http://192.168.0.1 and press Enter
3. Type the user name and password for the admin
Fig. 1
4. Click the "Wireless" button on the left
5. Under Wireless Settings, Security: select WPA-PSK
6. Supply a strong excellent Passphrase or password and confirm
7. Click Apply
Fig. 3
-------
How to limit the DHCP IP Address Range of the Router (D-Link DI-524) in your Home Network
1. Open an Internet Explorer browser
2. Type in the address bar http://192.168.0.1 and press Enter
3. Type the user name and password for the admin
Fig. 1
4. Click "DHCP" button on the left
When you bought your D-Link DI-524 Router, it has been pre-configured by default to assign dynamic (temporary) ip addresses from a range of 100, that is why you see the last 3 digits of the Starting IP Address 100 and the Ending IP Address 199 (this means that the Router can assign 192.168.0.100, 192.168.0.101, 192.168.0.102, 192.168.0.103, and so on, 192.168.0.198, up to 192.168.0.199 being the last, for a total of a hundred temporary or dynamic ip addresses)
Fig. 4
5. To limit the IP Range only to two, edit the last 3 digits of the Starting IP Address 100 and the Ending IP Address 101
6. Click Apply
Fig. 5
-------
How to configure the Router to assign Static DHCP IP Address and Setup the File Server computer & DNS Server to obtain Static IP Addresses
1. Properly connect the Ethernet network cable from the Router to the Server computer
2. Click Start --> Run
3. Type cmd
4. Press Enter
fig
5. In the Windows prompt,
Type "ipconfig /all"
Obtain the following information,
Windows IP Configuration:
Host name ---> Server name
Ethernet adapter: Integrated Controller (Network Interface Card, NIC)
Physical address ---> Server MAC address
IP Address ---> Server IP Address
Subnet mask ----> 255.255.255.0
Default Gateway (Router) ---> 192.168.0.1
DNS Servers ---> 192.168.0.1
fig
6. Open an Internet Explorer browser
7. Type in the address bar http://192.168.0.1 and press Enter
8. Type the user name and password for the admin
Fig
9. Click DHCP at the bottom left
10. Set the DHCP Server to "Disabled" (to prevent IP Reserver Error from the Router)
11. Set Static DHCP to "Enabled"
12. From the information taken from "ipconfig /all",
- Type the Server name
- Type the Server IP Address
- Server MAC Address
13. Click Apply
fig
14. The Router responds with a message
"The device is restarting..."
15. Press Continue
fig
16. Under Static DHCP Client List, you should see below the
Host name ---> Server name (this is the name of the File Server Computer)
fig
17. Set the DHCP Server to "Enabled"
18. Set the Static DHCP to "Enabled"
19. When both the DHCP Server and Static DHCP are set to "Enabled", click Apply
fig
20. When everything is done correctly, you should see:
Static DHCP Client List ---> Server
Dynamic DHCP Client List ---> Laptop 1 and Laptop 2
fig
21. Start ---> Control Panel ---> Double click "Network Connections"
fig
22. Under LAN or High-Speed Internet, click "Local Area Connection"
fig
23. Under Network Tasks, click "Change settings of this connection"
24. Under Local Area Connection Properties, on the "General" tab, find and click Internet Protocol (TCP/IP) from the drop-down list
25. Click Properties
26. Click the Radio Button to "Use the following IP Address:"
from the information taken from ipconfig /all,
IP Address: type the Server IP Address
Subnet mask: 255.255.255.0
Default gateway: 192.168.0.1
27. Under Use the following DNS Server addresses
Preferred DNS Server: 192.168.0.1
Alternate DNS Server:
28. Press Ok
29. Under Local Area Connection Properties, on the "General" tab, Internet Protocol (TCP/IP) ---> click Ok
30. This is the graphic representation diagram of your Home Network.
Pictures:
Subscribe to:
Posts (Atom)


















































